High level feature notes for code scanner integrations -Scan a set of pre-defined repositories to identify Org-level sensitive data within codebase -Repositories can be scanned in the following ways: Polymer DLP VCO for Github & Bitbucket Get it here Features *Contact us for Enterprise features and additional support options Polymer protects against data loss (DLP) […]

Are CASBs the panacea for cloud security?
A cloud access security broker (CASB) is a software tool or service that sits between an organization’s on-premises infrastructure and a cloud provider’s infrastructure. A CASB is the security guard allowing the organization to extend security frameworks on private and public cloud environments. We look into the features, benefits and shortcomings of CASB solutions in this article. 4 features […]
Database access controls & hidden data breach risks
Most data breaches from inside the organizations are still due to unfettered database access. It is critical for any executive to have a basic understanding of what database controls look like from a practical standpoint and understand off-the-radar areas of data breach risk. Typical onboarding of an employee or contractor requires assigning database access. […]
7 Team culture tips to drive cybersecurity & privacy
The best cybersecurity and privacy regimes will never work if your team members do not actively protect company efforts. Here is the precursor to how top-down security infrastructures have shortcomings. Instead, think how you can drive security from the ground up: with the support of each and every team member that contributes to your project. Here […]

Privileged access of information in an enterprise: brief History & the future
Perimeter security has historically provided the analogy of protecting the keys to the kingdom for Enterprises. Once you have been approved to enter the drawbridge which typically consists of verifications such as password, VPN, 2-Factor, a user can have access to all the data and applications within the castle. However once you are in the […]

Using natural language processing (NLP) based sentiment analysis for risk & trading: mixed bag!
We have built and/or integrated various machine learning (ML) models over the years within Financial Services. The success of these projects generally lie in tight requirements and good data quality. Following are some takeaways based on NLP work we did for an investment bank’s trading desk based in NYC (used with permission of course). Reason […]

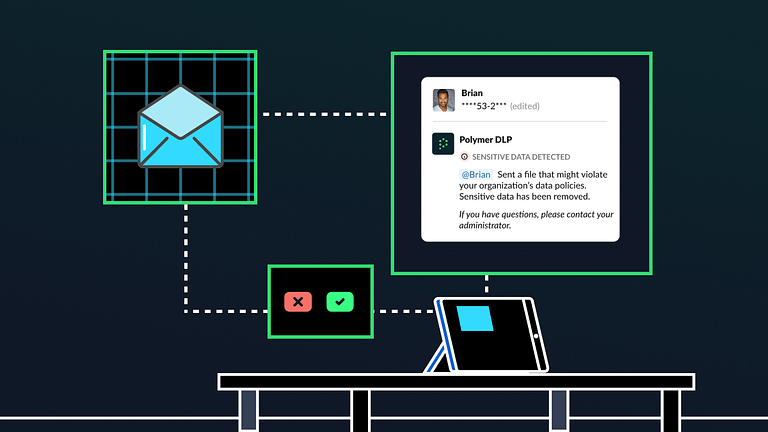
Is your codebase leaking sensitive data?
Pressure leads to shortcuts. Commenting in code is one of those shortcuts and shortcuts can introduce risks. A typical issue with commented code? Confidential data is left exposed. Maybe the programmer intended to edit it out – or simply didn’t think of it as consequential. Comments with exposed data is not a huge issue when […]
Offshore development teams: data breach & security risks abound!
Large number of businesses leverage offshore technology teams. However, very few of those companies have data governance on customer data nor understanding of the cyber-security risks involving some amazing and cheap talent. Chances of breaching GDPR, CCPA and other global privacy regulations is high when working with offshore development teams. Risks of working with remote and […]

Compliance challenges in client facing chats on Zoom/Slack/Zendesk et al
Client facing Slack and Zoom channels are especially useful for the direct and safe communication and support environment. For this reason, these client-facing chat rooms can also act as sources of sensitive data leaks, commercial chatter that could affect stock price or highly confidential data that stays is memorialized in ‘history’. Efficiency and organization at […]
Third-Party Apps on Slack: Lurking Data Security Threat
Many Slack users are unaware of the permissions that may become enabled when third-party applications are linked with one’s Slack account. According to the Slack Help Center, “an app’s permission scopes depend on the kinds of things it’s supposed to do.” Typically, such permissions may encompass the ability to view information, post information, and carry out […]

SOC2, ISO or HIPAA Compliance: False Sense of Security
In the US alone, the overall cost of healthcare breaches in 2019 was US$ 11.8 billion (£9.2 billion) – more than double the 2018 figure, & healthcare breach discovery time is the longest for any industry. Technology and process audits such as SOC2, ISO and HIPAA compliance certificate often creates a false sense of security […]


