Data is the lifeblood of the modern organization, and the number of data sources companies generate and use is growing by the day. Data takes many shapes and forms, meaning it can be difficult to structure and organize it. In fact, much of today’s enterprise data exists in silos, segmented by departments, geographies and even […]

What type of security tests should you use?
Security certifications such as SOC2, ISO27001 are great for an overall assessment of your tech and data governance posture. However these certifications are somewhat subjective and do not reflect an organization’s ability to withstand external cyber attacks or breach risks. In a cloud hosted environment with growing Shadow IT, data breach increases dramatically. Collaborative software […]

A beginner’s Guide to XDR: Extended Detection & Response
Definition Features of XDR What Makes XDR Different Advantages Challenges XDR Stats What is XDR? Recent research from Microsoft shows that cyber criminals – and their attacks – are becoming more sophisticated. Online criminals are using techniques that make them harder to detect. Naturally, to fight this complex threat, cyber security solutions also need to […]

What is ISO 27701? How is it different from ISO 27001?
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) are recognized internationally as authorities on management systems and best practice. ISO/IEC has become a gold standard to satisfy privacy, compliance and security posture especially as it relates to fintechs and healthcare providers. It is a great way to prove your compliance to […]
What is endpoint security, & why it’s critical in the post-covid era
According to Gartner research, between 30 and 40% of employees will continue to work remotely after the end of the pandemic. It’s clear that distributed work is here to stay. So, it’s time for IT teams to rethink their strategy and build a security stack that is appropriate for the remote world. The first line […]

4 Examples of data leaks from 3rd party SaaS apps [3 min video]
This video explains the risks of sensitive data leaks on collaborative platforms such as:

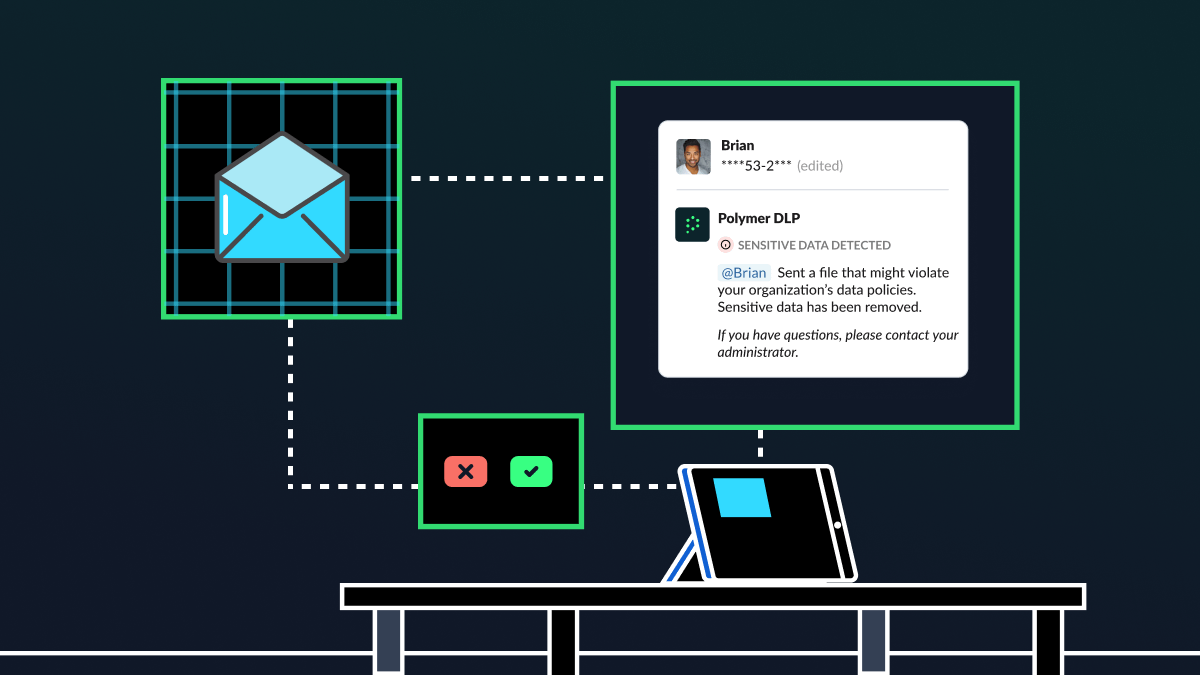
Why do DLP solutions suck?
Data loss protection products were once hailed as the panacea of security programs. Now they are more likely to be deemed as an expensive investment, with low ROI and a high amount of time-suck for security teams that barely use them. DLPs are supposed flag sensitive data exfiltration and give insights into what applications are […]

HIPAA privacy rules for non-covered entities
HIPAA data governance extends beyond doctors and healthcare providers to most entities providing services in the healthcare area. Understanding the role and responsibilities of the service providers is essential. The American Medical Association (AMA) now requires non-HIPAA-covered entities to protect sensitive Patient Health Information (PHI) they collect. In this third blog of our HIPAA blog […]

Electronic health records: necessary security safeguards
Second in our HIPAA blog series, this post takes a closer look at HIPAA’s technical safeguards. For starters, there are five technical safeguards as outlined in the HIPAA Security Rule. The primary purpose of these safeguards is to help healthcare providers ensure that electronic Protected Health Information (ePHI) is safe from data breach and security-related […]

Data breach risks from Microsoft Teams
Microsoft Teams has rapidly turned out to be the to-go-to application for remote work, accelerating exponentially in usage over the last twelve months. Teams boasts an impressive 145 million active daily users, marking a 26 percent increase up from 115 million daily active users in October 2020. However, despite the intrinsic trust, the success of […]

Secure access service edge: What is SASE?
The Software-as-a-Service (SaaS) industry is forecast to generate $157 billion by 2022, as more and more organizations move their workloads to the cloud and embrace the world of hybrid work. As companies increase their dependency on the cloud, however, they will likely experience latency and cost issues. This is because the traditional way of backhauling traffic through […]